Need The newest 70-689 Exam Dumps? Why not try PassLeader’s 299q 70-689 vce dumps or pdf dumps? Recntly, the 70-689 exam has been changed with a lot of new questions, old version 70-689 vce dumps or practice tests are not valid now, if you want to pass exam 70-689 easily, please download the latest update 299q 70-689 braindumps from PassLeader. Now visit passleader.com and you will get all the 70-689 study materials including free 70-689 study guide with valid 70-689 vce dumps and free vce player, which will help you passing exam easily!
keywords: 70-689 exam,299q 70-689 exam dumps,299q 70-689 exam questions,70-689 pdf dumps,70-689 vce dumps,70-689 vce test software,70-689 practice test,Microsoft Upgrading Your Skills to MCSA Windows 8
QUESTION 231
Your network contains an Active Directory domain. The domain contains client computers that run Windows 8 Enterprise. Users frequently use USB drives to store sensitive files that are used on multiple computers. Your corporate security policy states that all removable storage devices, such as USB data drives, must be encrypted. You need to ensure that if a user forgets the password for a USB disk that is encrypted by using BitLocker To Go, the user can resolve the issue themself. What should you do?
A. Instruct the user to open BitLocker Drive Encryption, select Backup Recovery Key, and then select Save to your Microsoft account.
B. Instruct the user to open BitLocker Drive Encryption, select Backup Recovery Key, and then select Print the recovery key.
C. Implement the BitLocker Network Unlock feature.
D. Publish a data recovery agent certificate by using a Group Policy object (GPO).
QUESTION 232
You have laptops that run Windows 8. The laptops have Microsoft User Experience Virtualization (UE-V) installed. You need to ensure that the application settings, which are synchronized by using UE-V, apply to computers that are disconnected from the network. What should you do?
A. From a command prompt, run sc config PeerDistSvc start=auto.
B. From Group Policy Management Editor, configure the Windows Connection Manager settings.
C. From a command prompt, run sc config CscService start=auto.
D. From Group Policy Management Editor, configure the Network Connections settings.
Answer: C
Explanation:
Problem: UE-V Agent installation fails with error: The Offline Files service is not running Cause: The UE-V Agent installation failed because Offline Files was not enabled on the system. Resolution: To resolve the issue, enable Windows Offline files on the system.
Windows 7 and Windows 8
Run the following command from an elevated command prompt:
sc config cscservice start=auto
QUESTION 233
Your company has a main office and a branch office. Each office contains several servers that run Windows Server 2012. You need to configure BranchCache for the client computers in the branch office. The solution must ensure that all of the cached content is in a central location. What should you run on each client computer?
A. the netdom command
B. the Enable-BCHostedClient cmdlet
C. the Enable-BCDistributed cmdlet
D. the winrm command
Answer: B
Explanation:
Enable-BCHostedClient
Configures BranchCache to operate in hosted cache client mode.
Note:
* BranchCache is designed to reduce WAN link utilization and improve application responsiveness for branch office workers who access content from servers in remote locations. Branch office client computers use a locally maintained cache of data to reduce traffic over a WAN link. The cache can be distributed across client computers (Distributed Cache mode) or can be housed on a server in the branch (Hosted Cache mode).
* BranchCache is disabled by default on client computers. Take the following steps to enable BranchCache on client computers:
Turn on BranchCache.
Enable either Distributed Cache mode or Hosted Cache mode. Configure the client firewall to enable BranchCache protocols.
QUESTION 234
You have client computers that run Windows 8 Pro. You need to recommend a solution to roll back the Windows Defender engine and the malware signature files on the computers. The solution must minimize administrative effort. What should you include in the recommendation?
A. File History
B. the Program and Features Control Panel item
C. Windows 7 File Recovery
D. System Restore points
Answer: D
Explanation:
A restore point is a representation of a stored state of your computer’s system files. You can use a restore point to restore your computer’s system files to an earlier point in time.
QUESTION 235
Hotspot Questions
You have several client computers that run Windows 7. The computers have identical hardware and software. The system properties of one of the computers are configured as shown in the following exhibit. (Click the Exhibit button.)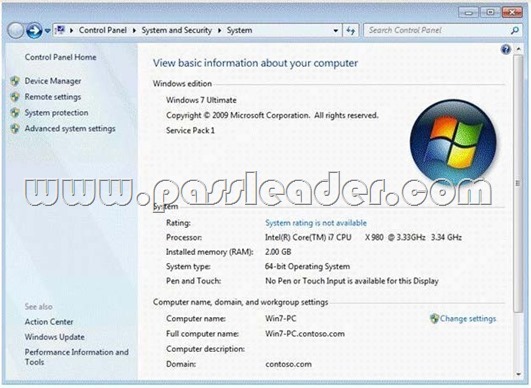
To answer, complete each statement according to the information presented in the exhibit. Each correct selection is worth one point.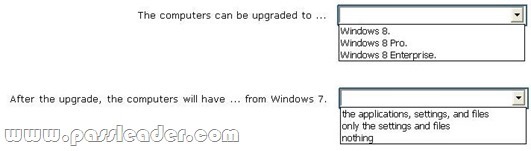
Answer: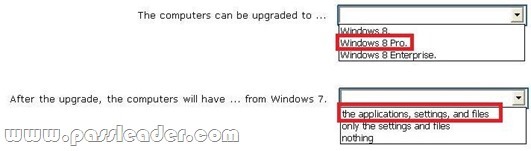
Explanation:
Note: You can upgrade to Windows 8 Pro and keep Windows settings, personal files, and applications from the following Windows operating system editions:
Windows 7 Starter
Windows 7 Home Basic
Windows 7 Home Premium
Windows 7 Professional
Windows 7 Ultimate
QUESTION 236
Hotspot Question
You install Windows 8.1 Enterprise on a new laptop that will be shipped to a remote user. You logon to the laptop with the user credentials, map network drives, and configure the network drives to be always available offline file synchronization. You need to prevent the user from creating files with a .dbl extension on the mapped drives. In the Local Group Policy Editor, which setting should you configure? (To answer, select the appropriate setting in the answer area.)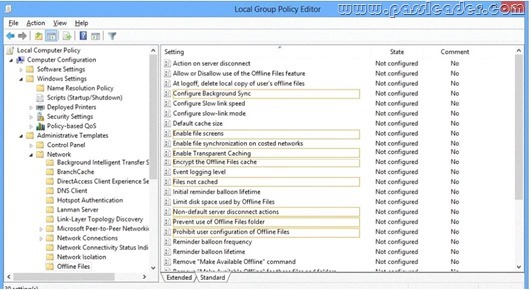
Answer: 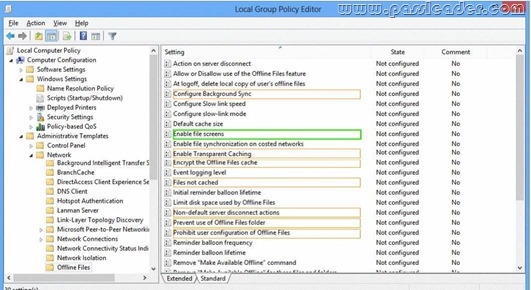
QUESTION 237
Drag and Drop Question
You manage Windows 8.1 client computers. You have the following client computer update requirements:
– Ensure that all client computers check for updates twice a day.
– Install all critical and available updates, including updates that require a restart, each day.
– Restart client computers at 11:00 P.M. if required.
– Distribute all updates from a Windows Server Update Services (WSUS) server on the local network.
You need to deploy Group Policy settings to the client computers to meet the update requirements. Which Group Policy settings should you enable and configure? (To answer, drag the appropriate Group Policy settings to the correct location or locations in the answer area. Group Policy settings may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.)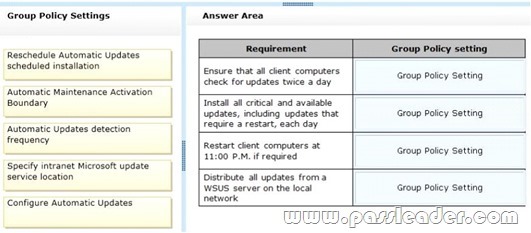
Answer: 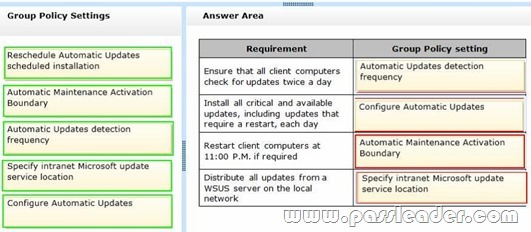
QUESTION 238
Drag and Drop Question
A company has Windows 8.1 client computers. All computers have the same hardware and software installed. The Development and Sales departments have different backup requirements. The requirements are described in the following table.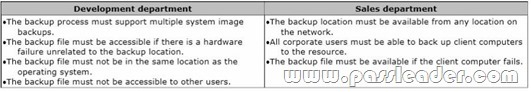
You need to select a backup location for each department. What should you do? (To answer, drag the appropriate resource to the correct location or locations in the answer area. Resources may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.)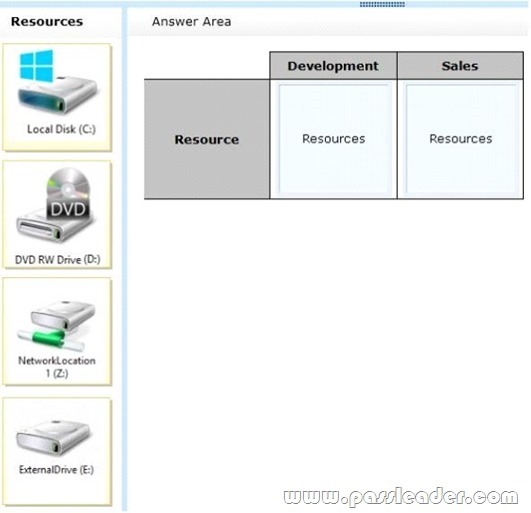
Answer: 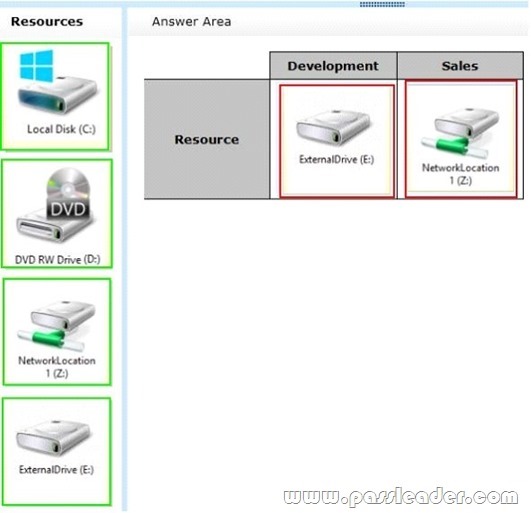
QUESTION 239
Your company has five hardware builds for client computers. The hardware builds are configured as shown in the following table.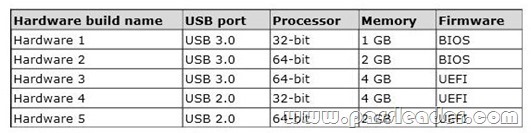
You plan to provide some users with Windows To Go disks that contain a corporate image of the 64-bit version of Windows 8 Enterprise and several line-of-business (LOB) applications. In the table below, identify whether the hardware build is compatible or incompatible with the Windows To Go disks. Make only one selection in each row. Each correct selection is worth one point.
Answer: 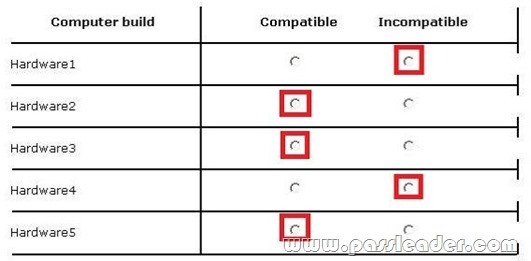
Explanation:
* Windows To Go is a feature in Windows 8 Enterprise that allows Windows 8 Enterprise to boot and run from mass storage devices such as USB flash drives and external hard disk drives.
* 64-bit Windows 8 Enterprise cannot run on 32-bit processors.
* Both USB 2.0 and USB 3.0 work fine with Windows to Go.
* The Unified Extensible Firmware Interface (UEFI) (pronounced as an initialism U-E-F-I or like “unify” without the n) is a specification that defines a software interface between an operating system and platform firmware. UEFI is meant to replace the Basic Input/Output System (BIOS) firmware interface, present in all IBM PC-compatible personal computers. In practice, most UEFI images provide legacy support for BIOS services.
* The Windows 8 Enterprise 2 GB RAM requirement is meet by the 64-bit profiles.
QUESTION 240
Hotspot Questions
You have 10 Windows 8.1 Pro client computers. The Storage Spaces settings of the computers are configured as shown in the following exhibit. (Click the Exhibit button.)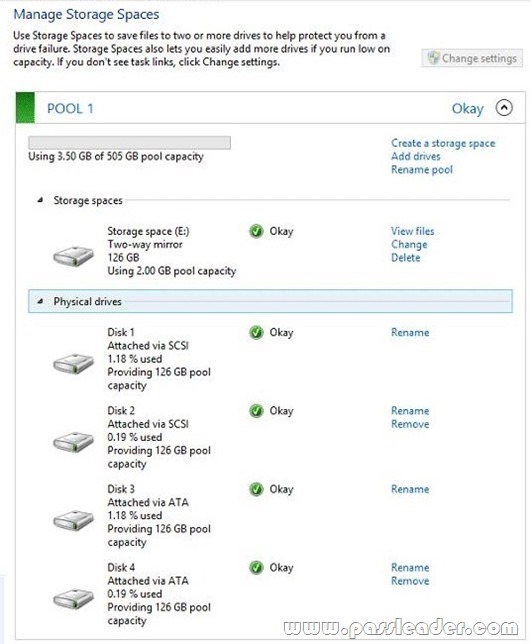
To answer, complete each statement according to the information presented in the exhibit. Each correct selection is worth one point.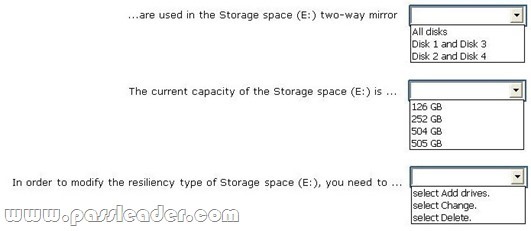
Answer: 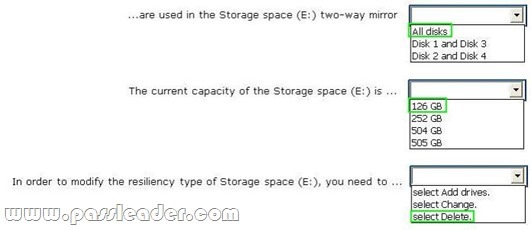
70-689 exam dumps, 70-689 exam questions, 70-689 vce dumps, 70-689 pdf dumps, 70-689 practice test, 70-689 study guide: http://www.passleader.com/70-689.html
QUESTION 241
Hotspot Questions
Your company has a main office and a branch office. You have client computers that run Windows 8 Enterprise. You are evaluating whether to disable IPv6 on the client computers in the sales, marketing, research, and finance departments. Each user in the sales department has a laptop and frequently accesses the network by using DirectAccess. Each user in the marketing department has a desktop computer located in the branch office. All of the marketing department computers are configured to use BranchCache. Each user in the research department has a desktop computer located in the main office and uses IPSec to access research servers. Each user in the finance department has a laptop and frequently accesses the network by using an SSTP VPN connection. In the table below, identify which departments require IPv6 and which departments do not require IPv6. Make only one selection in each row. Each correct selection is worth one point.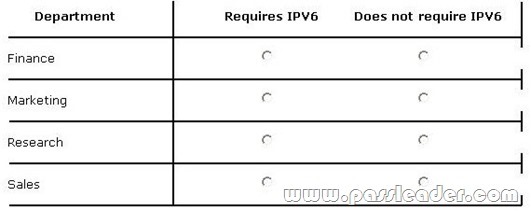
Answer: 
QUESTION 242
Hotspot Questions
Your company has client computers that run Windows 8 Enterprise and Windows RT. The company has a subscription to Windows Intune. You plan to deploy line-of-business (LOB) Windows Store apps to all of the computers by using Windows Intune. The LOB apps will be signed by using a certificate issued by a trusted certification authority (CA). You need to prepare all of the computers for the deployment of the LOB Windows Store apps. In the table below, identify on which operating system each task should be performed. Make only one selection in each row. Each correct selection is worth one point.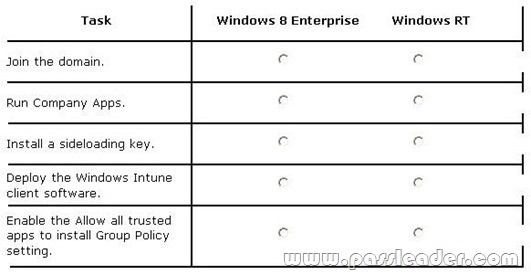
Answer: 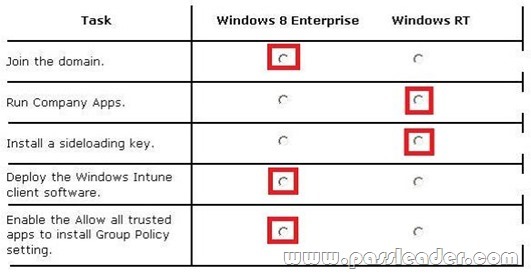
QUESTION 243
You have client computers that run Windows 8 Enterprise. The network contains a network printer. Users connect to the printer by using a local TCP/IP port. A network administrator changes the IP address of the printer. You need to create a script to update the IP address used by the local TCP/IP port on the computers. Which two Windows PowerShell cmdlets should you run? (Each correct answer presents part of the solution. Choose two.)
A. Add-PrinterPort
B. Add- PrinterD river
C. Set-PrinterConfiguration
D. Add-Printer
E. Set-Printer
Answer: AE
Explanation:
A: Add-PrinterPort
Installs a printer port on the specified computer.
Parameters include:
-PortNumber<UInt32>
Specifies the TCP/IP port number for the printer port added to the specified computer.
E: Set-Printer
Updates the configuration of an existing printer.
Parameters include:
-PortName<String>
Specifies the name of the port used or created for the printer.
QUESTION 244
Your network contains client computers that run Windows 8 Enterprise. The computers are members of an Active Directory domain. Your company purchases a subscription to Windows Intune. Synchronization between Active Directory and Windows Intune is not configured. You enroll all of the computers in Windows Intune. You plan to create groups that contain the computers by using dynamic membership. You need to identify which criteria you can use to populate the groups dynamically. Which three criteria should you identify? (Each correct answer presents a complete solution. Choose three.)
A. organizational unit (OU)
B. manager
C. security group
D. device type
E. domain
Answer: ABC
Explanation:
Windows Intune Dynamic membership query criteria include:
Security group
Manager
Organizational unit (OU)
Note:
* A group can have direct members (static membership), dynamic query-based members, or both. When you create a dynamic membership query, you define the criteria that determines the query that Windows Intune runs to retrieve the list of group members. The group is automatically updated with members that meet the criteria whenever changes occur. You can also create groups that have static membership lists. These are groups that you manually define by explicitly adding members.
* Windows Intune is a Microsoft cloud-based management solution. Intune is primarily aimed at small and medium enterprises and service providers who want to manage up to 500 Microsoft Windows computers. Distribution is through a subscription system in which a fixed monthly cost is incurred per PC. The minimum subscription duration is one year. Included in the package is the Windows operating system, currently Windows 8 Enterprise.
QUESTION 245
Your company has client computers that run Windows 8. All of the computers have the SkyDrive desktop application installed. Windows 7 File Recovery is configured to create a local backup of Microsoft Office 2013 documents. Only one backup is retained. A user deletes a Microsoft Word document from his computer. The document was located in a SkyDrive synchronized folder. You need to recover the document, including the previous versions of the document. What should you use?
A. the Recycle Bin on the desktop
B. the SkyDrive website
C. Windows 7 File Recovery
D. the SkyDrive desktop application
Answer: B
QUESTION 246
Your network contains a Microsoft Exchange Server 2013 organization. You have an Exchange ActiveSync policy that has the following settings configured:
– AllowRemoteDesktop
– AllowInternetSharing
– RequireDeviceEncryption
– MinDevicePasswordLength
– AllowSimpleDevicePassword
You need to identify which settings are applied to devices that run Windows RT. Which three settings should you identify? (Each correct answer presents part of the solution. Choose three.)
A. MinDevicePasswordLength
B. AllowRemoteDesktop
C. AllowInternetSharing
D. RequireDeviceEncryption
E. AllowSimpleDevicePassword
Answer: ADE
Explanation:
Windows 8\RT Supported Policy Parameters for EAS mailbox policies for Exchange Server 2013 are:
(A) MinDevicePasswordLength
(D) RequireDeviceEncryption
(E) AllowSimpleDevicePassword
PasswordEnabled
MinDevicePasswordComplexCharacters
MaxInactivityTimeDeviceLock
DevicePasswordHistory
MaxDevicePasswordFailedAttempts
AllowNonProvisionableDevices
DevicePasswordExpiration
Note:
* Windows RT is a new Windows-based operating system that’s optimized for thin and light PCs that have extended battery life and are designed for life on the go. Windows RT only runs built-in apps or apps that you download from the Windows Store. Windows Update automatically keeps your PC up to date and Windows Defender provides up-to-date virus and malware protection.
QUESTION 247
Hotspot Questions
You have a client computer that runs Windows 8 Pro. The computer contains a storage pool. You need to remove a disk named Disk 2 from the storage pool. What should you configure first? (To answer, select the appropriate option in the answer area.)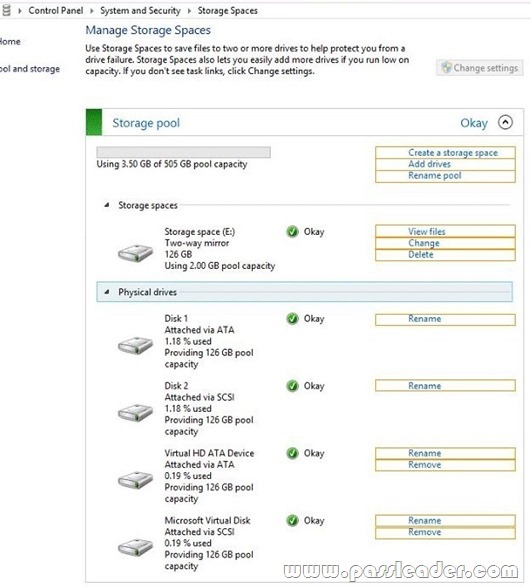
Answer: 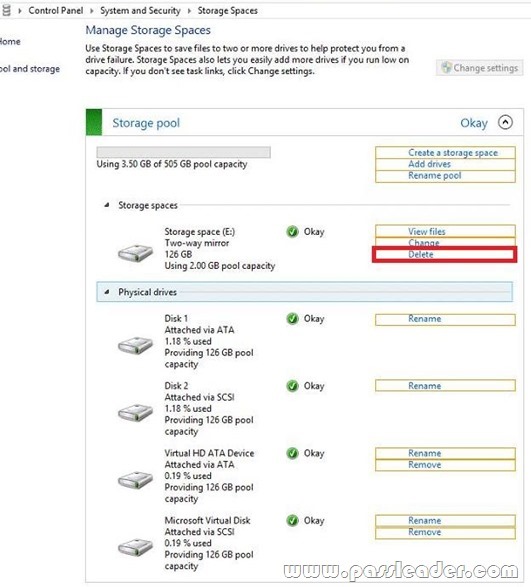
QUESTION 248
Your network contains an Active Directory domain. All client computers run Windows 8 Enterprise. Microsoft System Center 2012 Endpoint Protection is deployed to all of the computers by using the default settings contained in the Default Antimalware Policy. The users in the research department report that a folder named C:\TestApp must not be scanned by the Endpoint Protection client. You need to configure the Endpoint Protection client not to scan the C:\TestApp folder for the computers in the research department only. What should you do first?
A. In the Endpoint Protection client, modify the Excluded files and locations setting for each research department computer.
B. Create a new antimalware policy and modify the Threat overrides settings.
C. Create a new antimalware policy and modify the Exclusion settings.
D. In the Default Antimalware Policy, modify the Exclusion settings.
Answer: C
QUESTION 249
Hotspot Questions
You have a folder that you plan to share. You need to configure security for the shared folder to meet the following requirements:
– Members of a security group named Group1 must be able to modify permissions of files and folders.
– Members of a security group named Group2 must be able to read files and folders only.
– Members of a security group named Group3 must be able to take ownership of files.
What should you do? (To answer, select the appropriate options in the answer area.)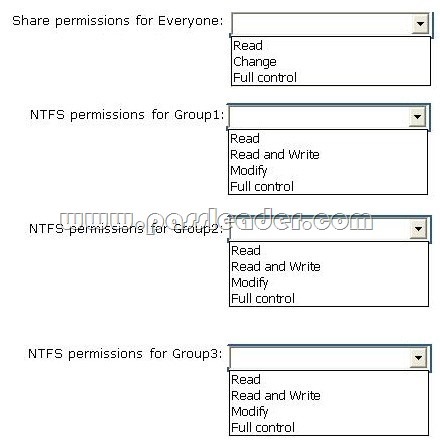
Answer: 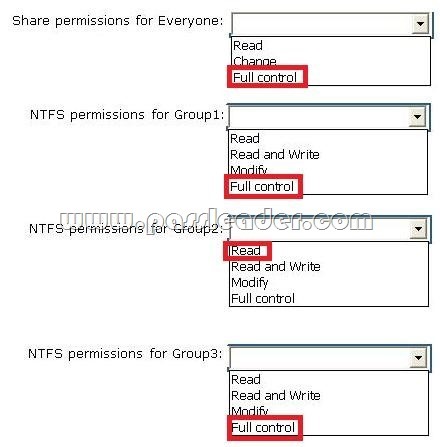
QUESTION 250
Hotspot Questions
Your network contains an Active Directory forest named adatum.com. The forest contains three domains named adatum.com, na.adatum.com, and eu.adatum.com. You have a client computer named Computer1 that runs Windows 8 Enterprise. Computer1 is a member of the na.adatum.com domain. You need to ensure that single-label names can be resolved from all three domains. Which setting should you configure? (To answer, select the appropriate setting in the answer area.)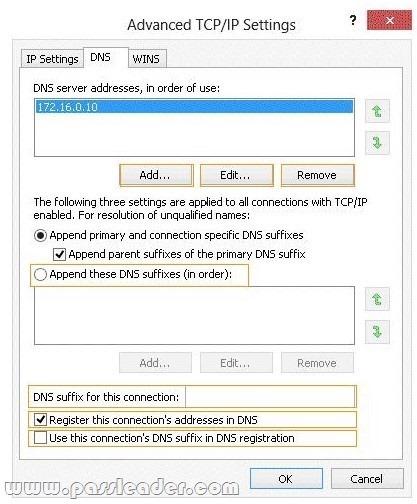
Answer: