Get New Valid 70-680 Exam Dumps To Pass Exam Easily: The following new 70-680 exam questions were updated in recent days by PassLeader, visit passleader.com to get the full version of new 580q 70-680 exam dumps with free version of new VCE Player software, our valid 70-680 briandumps will help you passing 70-680 exam easily! 70-680 PDF practice test and VCE are all available now!
keywords: 70-680 exam,580q 70-680 exam dumps,580q 70-680 exam questions,70-680 pdf dumps,70-680 vce dumps,70-680 braindumps,70-680 practice test,70-680 study guide,TS: Windows 7, Configuring Exam
QUESTION 321
You have a computer that runs Windows XP. The computer has one basic disk that contains a single partition. The partition has 30 GB of free space. The hard disk has 5 GB of unallocated space. You need to install Windows 7 in a dual-boot configuration. Windows 7 must not be installed in a virtual hard disk (VHD). What should you do first?
A. Create a second partition.
B. Shrink the primary partition.
C. Convert the hard disk to a GPT disk.
D. Convert the hard disk to a dynamic disk.
Explanation:
Given the system requirements more space is required. There is not enough unallocated space so the XP partition will need to be shrunk first, in order for a sufficient sized partition to be created.Requirements: Windows 7 Home Premium, Professional, Ultimate, and Enterprise editions have the following minimum hardware requirements: – 1 GHz 32-bit (x86) or 64-bit (x64) processor – 1 GB of system memory – A 40-GB hard disk drive (traditional or SSD) with at least 15 GB of available space – A graphics adapter that supports DirectX 9 graphics, has a Windows Display Driver Model (WDDM) driver, Pixel Shader 2.0 hardware, and 32 bits per pixel and a minimum of 128 MB graphics memory
QUESTION 322
You have a computer that runs Windows 7. The computer is a member of a domain. You share D:\data as Data. You assign Everyone Full control share permissions to the folder. No other share permissions are assigned to the folder. From another computer, you attempt to create a file in the Data share by using a domain account named User1. You receive the following error message:
“Destination Folder Access Denied.”
You need to ensure that you can create files in the Data share by using the User1 account. What should you do?
A. Create a local user named User1.
B. Add User1 to the local Power Users group.
C. Assign User1 Write NTFS permission on the D:\data folder.
D. Assign User1 Full control share permissions to the Data share.
Answer: C
Explanation:
Share permissions apply to users who connect to a shared folder over the network. Share permissions do not affect users who log on locally, or log on using Remote Desktop. To set permissions for users who log on locally or using Remote Desktop, use the options on the Security tab instead of the Share Permissions tab. This sets permissions at the NTFS file system level. If both share permissions and file system permissions are set for a shared folder, the more restrictive permissions apply when connecting to the shared folder. For example, to give Read access on a shared folder to users in your domain, on the Share Permissions tab, set permissions for the Everyone group to Full Control. On the Security tab, specify more restrictive access by setting the permissions for the Domain Users group to Read access. The result is that a user who is a member of the Domain Users group has read-only access to the shared folder whether the user is connected through a network share, through Remote Desktop, or is logged on locally. Permissions The Read permission allows a user or group to access a file or folder but does not allow modification or deletion. The Change permission includes the read permission but also allows you to add files, delete files, and modify files in the shared folder. This permission is equivalent to the Read/Write permission in the basic File Sharing dialog box. The Full Control permission includes all the rights conferred by the Change and Read permissions. It also allows the user assigned that permission to modify the permissions of other users. Full Control is equivalent to the basic sharing Owner permission, though unlike basic sharing, where there can only be one user assigned the Owner permission, you can assign the Full Control permission to users and groups. NTFS permissionsYou can configure the local NTFS permissions for a shared folder or volume using Share and Storage Management in the following ways: New shared resources. In the Provision a Shared Folder Wizard, before you select a network sharing protocol, you can change the NTFS permissions for the folder or volume you will be sharing. These NTFS permissions will apply both locally and when accessing the resource over the network. To change the NTFS permissions, on the NTFS Permissions page, select Yes, change NTFS permissions, and then click Edit Permissions. Existing shared resources. You can change the NTFS permissions of a shared folder or volume listed on the Shares tab. To change the NTFS permissions, select the folder or volume, in the Actions pane click Properties, and on the Permissions tab, click NTFS Permissions.
QUESTION 323
Your network contains a Network Policy and Access Services server named Server1. All certificates in the organization are issued by an enterprise certification authority (CA) named Server2. You have a standalone computer named Computer1 that runs Windows 7. Computer1 has a VPN connection that connects to Server1 by using SSTP. You attempt to establish the VPN connection to Server1 and receive the following error message:
“A certificate chain processed, but terminated in a root certificate which is not trusted by the trust provider.”
You need to ensure that you can successfully establish the VPN connection to Server1. What should you do on Computer1?
A. Import the root certificate of Server2 to the user’s Trusted Publishers store.
B. Import the root certificate of Server2 to the computer’s Trusted Root Certification Authorities store.
C. Import the server certificate of Server1 to the user’s Trusted Root Certification Authorities store.
D. Import the server certificate of Server1 to the computer#s Trusted Root Certification Authorities store.
Answer: B
Explanation:
A certificate chain establishes a “chain of trust” from a certification authority (CA) to an individual certificate. Trust occurs if a valid certificate from that CA can be found in your root certificate directory. As long as you trust the CA, you will automatically trust any other certificates signed by that CA.
QUESTION 324
You have a computer that runs Windows 7. The computer contains a folder named C:\data. You use Advanced Sharing to share C:\data by using the default share permissions. When a user tries to access the share over the network, he gets an Access is Denied error message. You need to ensure that the user can access the share. What should you do?
A. Allow file and printer sharing through Windows Firewall.
B. Change the network location from a Public network to a Home or Work network.
C. From the Security settings of the folder, assign the user the Read NTFS permission.
D. From the Advanced Sharing settings of the folder, assign the user the Read share permission.
Answer: C
Explanation:
Advanced Security Settings Properties Page – Permissions Tab You can add additional resources, groups or users to have explicit NTFS permissions to access this object, or you can edit or remove the NTFS permissions granted to a resource, group, or user on the object. Inherited permissions are those that are propagated to an object from a parent object. Inherited permissions ease the task of managing permissions and ensure consistency of permissions among all objects within a given container.
QUESTION 325
You have a portable computer that runs Windows 7. The computer is joined to a domain. Multiple users log on to the computer. You need to prevent the computer from displaying the username of the last user who logged on. What should you do?
A. From Control Panel, modify the User Profiles settings.
B. From Control Panel, modify the Personalization settings.
C. From the local computer policy, add a policy template.
D. From the local computer policy, modify the local security policy.
Answer: D
Explanation:
How to Prevent the Last Logged-On User Name from Being Displayed
1. Click Start and type secpol.msc in the search box.
2. Press Enter.
3. Within the Local Security Policy, navigate to Security Settings | Local Policies | Security Options.
4. In the details pane, scroll through the options and locate Interactive logon: Do not display last user name.
5. Double click this security option and click Enabled.
6. Click OK.
QUESTION 326
You have a computer named Computer1 that runs Windows 7. You have a server named Server1 that runs Windows Server 2008. Computer1 and Server1 have IPv4 and IPv6 installed. You need to identify whether you can connect to Server1 by using IPv6. What should you do?
A. Run Ping Server1 -6.
B. Run Ping Server1 -n 6.
C. Run Net view \\Server1.
D. Open \\server1 from the Run dialog box.
Answer: A
Explanation:
Ping. The Ping tool is still widely used, although more firewalls block Internet Control Message Protocol (ICMP) echo requests than used to be the case. However, even if you cannot get past a firewall on your organization’s network, Ping is still useful. You can check that the IPv4 protocol is working on a computer by entering ping 127.0.0.1. You can then ping the IPv4 address of the computer. You can find out what this is by using the Ipconfig tool. If your computer has more than one interface combined in a network bridge, you can ping the Ipv4 address of the network bridge. When you have established that you can ping your computer using an Ipv4 address, you can test that DNS is working internally on your network (assuming you are connected to a DNS server, a WAP, or have ICS configured on your network) by pinging your computer name–for example, entering ping canberra. Note that if DNS is not implemented on your system, ping canberra still works because the IPv6 link-local address resolves automatically.
-6 Force using IPv6.
QUESTION 327
You have a computer that contains a DVD drive and a single 350-GB hard disk drive. You attempt to install Windows 7 on the computer by using the DVD installation media and receive the following error message:
“Reboot and Select proper Boot device or Insert Boot Media in selected Boot device.”
You need to ensure that you can install Windows 7 on the computer by using the DVD installation media. What should you do?
A. From the BIOS, modify the startup order.
B. From the BIOS, enable Pre-Boot Execution Environment (PXE).
C. Create an answer file named oobe.xml and place the file on the hard disk drive.
D. Create an answer file named autounattend.xml and place the file on the hard disk drive.
Answer: A
Explanation:
To install Windows 7 from a DVD-ROM, boot from the DVD-ROM drive and follow the prompts. You may need to configure the computer’s BIOS to support booting from DVD-ROM. If a computer does not have a DVD-ROM drive attached, you can still install from DVD-ROM–you just need to acquire a USB DVD-ROM drive. In this case, it will be necessary to configure the computer’s BIOS to boot from the USB device.
QUESTION 328
You have a computer that runs Windows 7. A user installs a third-party media player on the computer. You discover that all media files automatically open by using the third-party media player. You need to ensure that all media files open automatically by using Windows Media Player. You must achieve this goal by using the minimum amount of administrative effort. What should you do?
A. Select a media file. Right-click the file and select Open with.
B. Select a media file. Right-click the file and select Restore previous versions.
C. From Control Panel, modify the Set your default programs settings.
D. From Control Panel, modify the Set program access and computer defaults settings.
Answer: C
QUESTION 329
You deploy a custom image to a computer and discover that the Telnet Client feature is disabled. You need to ensure that the Telnet Client feature is enabled when you deploy the image. You must achieve this goal in the minimum amount of time. What should you do?
A. Enable the Telnet Client feature on the computer.
Generalize the computer and capture the image.
B. Create an unattended file that enables Telnet Client.
Generalize the computer and specify the unattended file. Capture the image.
C. Mount the image.
Run Ocsetup.exe TelnetClient.
Commit the changes and unmount the image.
D. Mount the image.
Run Dism.exe and specify /image and /enable-feature:TelnetClient switches.
Commit the changes and unmount the image.
Answer: D
Explanation:
NOTE: “when you deploy the image.” Implies for future installations, not the current one. Therefore the imagefile must be updated. Dism Deployment Image Servicing and Management (DISM) is a command-line tool used to service Windows?images offline before deployment. You can use it to install, uninstall, configure, and update Windows features, packages, drivers, and international settings. Subsets of the DISM servicing commands are also available for servicing a running operating system. Windows 7 introduces the DISM command-line tool. You can use DISM to service a Windows image or to prepare a Windows PE image. DISM replaces Package Manager (Pkgmgr.exe), PEimg, and Intlcfg in Windows Vista, and includes new features to improve the experience for offline servicing. You can use DISM to perform the following actions:
– Prepare a Windows PE image.
– Enable or disable Windows features within an image.
– Upgrade a Windows image to a different edition.
– Add, remove, and enumerate packages.
– Add, remove, and enumerate drivers.
– Apply changes based on the offline servicing section of an unattended answer file.
– Configure international settings.
– Implement powerful logging features.
– Service operating systems such as Windows Vista with SP1 and Windows Server 2008.
– Service a 32-bit image from a 64-bit host and service a 64-bit image from a 32-bit host.
– Service all platforms (32-bit, 64-bit, and Itanium).
– Use existing Package Manager scripts.
QUESTION 330
You have a computer that runs Windows 7. You install Internet Information Services (IIS) to test a web based application. You create a local group named Group1. You need to ensure that only the members of Group1 can access the default Web site. Which two configuration changes should you perform? (Each correct answer presents a part of the solution, Choose two.)
A. Modify the properties of Group1.
B. Assign an SSL certificate to the default Web site.
C. Modify the authentication methods of the default Web site.
D. Modify the NTFS permissions of the %systemroot%\inetpub\wwwroot folder.
Answer: CD
Explanation:
Modifying the Default Authentication Method. You can use the Directory Security tab of the Web Site Properties dialog box to change the authentication method. The authentication method determines whether users are identified, and how users must be identified to access your site. The authentication method you select varies, depending on the kind of site you are creating and the purpose of the site. Modify the NTFS permissions of the %systemroot%\inetpub\wwwroot folder
See article: How to set required NTFS permissions and user rights for an IIS 5.0, IIS 5.1, or IIS 6.0 Web server
http://support.microsoft.com/kb/271071
http://www.passleader.com/70-680.html
QUESTION 331
You have a computer that runs Windows 7. A user reports that he is unable to access network resources. You run Ipconfig.exe as shown in the IPConfig exhibit. (Click the Exhibit button.) 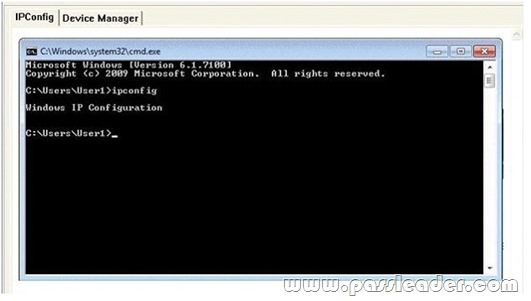
You open Device Manager as shown in the Device Manager exhibit. (Click the Exhibit button.)
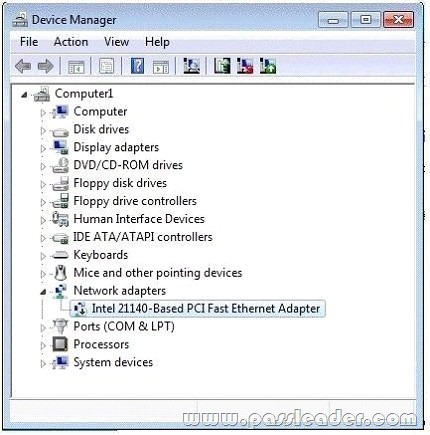
You need to ensure that the user can connect to the network. What should you do?
A. From Device Manager, enable the network adapter.
B. From Device Manager, update the driver for the network adapter.
C. At a command prompt, run Ipconfig /renew.
D. At a command prompt, run Netsh ip set address “local area connection” dhcp.
Answer: A
QUESTION 332
You have a computer that runs Windows 7. You install a third-party Web browser. You discover that HTML files are no longer associated with Windows Internet Explorer. You need to ensure that Internet Explorer starts whenever a HTML file is opened. What should you do from Internet Options?
A. Open the Connections tab and click Setup.
B. Open the General tab and click Use default.
C. Open the Programs tab and click Make default.
D. Open the Programs tab and click Manage add-ons.
Answer: C
Explanation:
Change your default web browser. This information applies to Internet Explorer 8 or Internet Explorer 7 running on Windows 7, Windows Vista, Windows Server 2008, Windows XP Service Pack 2 and Service Pack 3, and Windows Server 2003. To make Internet Explorer your default web browser
1. Click to open Internet Options.
2. Click the Programs tab, and then click Make default.
3. Click OK, and then close Internet Explorer.
QUESTION 333
You have a computer that runs Windows 7. You need to configure system image backups to meet the following requirements:
– Automatically create a system image every day without user intervention.
– Retain multiple copies of the system image.
Which type of backup destination should you use?
A. External hard disk drive
B. Network location
C. USB flash drive
D. Writeable DVD
Answer: A
Explanation:
Backup And Restore in Windows 7 supports backing up data files to CD-ROM, DVD-ROM, hard disk (including VHD files), or a network location. You can use Backup And Restore to write a System Image backup to an internal hard disk drive, an external hard disk drive (if formatted with the NTFS file system) and a network location.
You cannot use Backup And Restore to write a System Image backup to a USB flash drive, a writable DVD, or a tape drive. You need to schedule client computers that store important data for automatic backup. After you first configure automatic file backup using the Backup And Restore console, Windows 7 regularly backs up your files. The first time a backup is performed, a full backup is done, including all important user documents. Subsequent backups are incremental, backing up only changed files. Older backups are discarded if the disk begins to run out of space.Scheduling Backups with the Backup And Restore Console Windows 7 Backup uses shadow copies to take a snapshot of your files, allowing the backup to completely back up files even if they are open. Backups are configured and scheduled by using the Backup And Restore console under System And Security in Control Panel.
You can select the following types of backup destination: An external hard drive External hard drives are more expensive to purchase than internal hard drives, although you need to balance this against the cost of fitting the internal drive. They can be removed and stored in a secure location. However, they are typically slower than internal hard drives and tend to be less reliable, mainly because they are by default formatted using FAT rather than NTFS. You cannot use an external hard drive for a System Image backup unless you convert its filing system to NTFS. Because it is easily removable, it is more likely that an external hard drive will be missing when a scheduled backup is required.
Network locationIf your computer is short of disk space, you can back it up to a network location on another computer or network storage. Note that this is not the same as the situation in a production environment, where users’ Documents libraries are stored on a file server and an administrator backs up the file server.
You can save your backups on a network location only on computers running Windows 7 Professional, Windows 7 Ultimate, and Windows 7 Enterprise, and you need to provide credentials so that Windows Backup can access the network. Bear in mind that you can save your backups on a network location only on computers running Windows 7 Professional, Windows 7 Ultimate, and Windows 7 Enterprise.USB flash drivesFlash drive memory is considerably less expensive and flash drive devices support much more memory than they did three or even two years ago. Nevertheless, they typically support a lot less memory than hard drives and quickly fill up if you needed to keep copies of older backups.
You cannot save System Image backups to flash memory. A flash drive must be able to hold more than 1 GB if you want to save a backup on it. Flash drives can be stored offsite and are small and easy to carry. They are also easy to lose.
QUESTION 334
You have a computer that runs Windows 7 and Windows Internet Explorer 8. You open Internet Explorer and access a Web site. The Web site displays a page that has misaligned text and graphic image. You verify that the Web page displays correctly in previous versions of Internet Explorer. You need to view the Web page correctly. What should you do?
A. Modify the text size.
B. Enable Caret Browsing.
C. Enable Compatibility View.
D. Disable the SmartScreen Filter.
Answer: C
Explanation:
Internet Explorer Compatibility View. Internet Explorer Compatibility View allows sites designed for previous versions of Internet Explorer to display correctly for users of Internet Explorer 8. You can enable Compatibility View for a page by clicking the broken page icon at the end of the address bar. You can configure Compatibility View settings through the Compatibility View Settings dialog box. You can access this dialog box by clicking Compatibility View Settings on the Tools menu of Internet Explorer.
QUESTION 335
You have a computer that is certified for Windows 7. You need to install Windows 7 on the computer. The installation method must prevent you from being prompted for information during the installation. What should you do?
A. Create an unattend.txt file on a removable drive.
Start the computer from the Windows 7 installation media.
B. Create an autounattend.xml file on a removable drive.
Start the computer from the Windows 7 installation media.
C. Start the computer from the Windows 7 installation media.
At the command prompt, run Setup.exe and specify the /m parameter.
D. Start the computer from the Windows 7 installation media.
At the command prompt, run Setup.exe and specify the /tempdrive.
Answer: B
QUESTION 336
You have a computer that runs Windows 7. You open Windows Internet Explorer and access a Web site as shown in the exhibit. (Click the Exhibit button.) 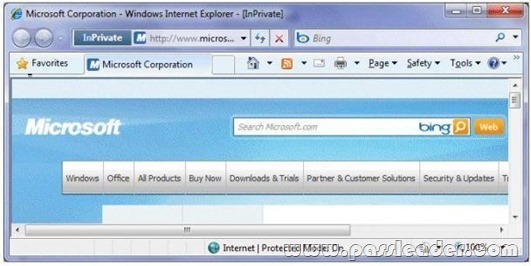
You click the Suggested Sites button, but the suggestions fail to display. You need to obtain suggested sites. What should you do?
A. From the Page menu, enable Caret Browsing.
B. From the Safety menu, disable the SmartScreen Filter.
C. From the Start menu, open a new Internet Explorer window.
D. From the Microsoft Corporation Web site, refresh the Suggested Sites Web Slice.
Answer: C
Explanation:
Opening a new Internet Explorer window will not open with InPrivate enabled. InPrivate is turned onInPrivate Browsing helps prevent Internet Explorer from storing data about your browsing session. This includes cookies, temporary Internet files, history, and other data. Toolbars and extensions are disabled by default. You must enable InPrivate Filtering manually each time you start a new browsing session.
QUESTION 337
You are evaluating the purchase a notebook computer that has the following hardware:
– 1.6 GHz 32-bit processor
– 1024 MB RAM
– 1 video card that uses shared memory
– 4 GB solid state drive
You need to ensure that you can install Windows 7 Enterprise on the notebook computer. Which hardware component should you change?
A. Hard disk
B. Processor
C. RAM
D. Video card
Answer: A
Explanation:
Hard Disk does not meet the minimum requirements.4-GB solid state drive!= 40-GB hard disk drive (traditional or SSD) with at least 15 GB of available spaceRequirements:Windows 7 Home Premium, Professional, Ultimate, and Enterprise editions have the following minimum hardware requirements:
– 1 GHz 32-bit (x86) or 64-bit (x64) processor- 1 GB of system memory
– A 40-GB hard disk drive (traditional or SSD) with at least 15 GB of available space
– A graphics adapter that supports DirectX 9 graphics, has a Windows Display Driver Model (WDDM) driver
– Pixel Shader 2.0 hardware, and 32 bits per pixel and a minimum of 128 MB graphics
QUESTION 338
You have a computer that runs Windows 7. You install Windows XP in a new partition on the computer and discover that you can no longer start Windows 7. You need to start Windows 7 in the minimum amount of time. What should you do?
A. From Windows XP, modify the default path in the boot.ini file.
B. From Windows XP Recovery Console, run the Fixboot command.
C. Start the computer from the Windows 7 installation media and select Install now.
D. Start the computer from the Windows 7 installation media and run Startup Repair.
Answer: D
Explanation:
When configuring a new computer to boot between multiple operating systems, it is also necessary to install operating systems in the order that they were released. For example, if you want to boot between Windows XP and Windows 7 on a new computer, you need to install Windows XP before you install Windows 7. If you install Windows XP after Windows 7, the Windows XP installation routine cannot recognize the Windows 7 operating system installation and the computer only boots into Windows XP. It is possible to repair the computer from this point using Windows 7 startup repair so that it dual-boots, but the simplest course of action is just to install the operating systems in the order in which they were released
QUESTION 339
Your company uses Windows Deployment Services (WDS) to deploy Windows 7. You create a new image of Windows 7. You need to ensure that you can deploy the image by using WDS. What should you do?
A. From the Windows Deployment Services snap-in, add a new install image.
B. From the Windows Deployment Services snap-in, add a new boot image.
C. Run Oscdimg.exe and specify the -boot parameter. Copy the image to C:\remoteinstall\boot.
D. Run Imagex.exe and specify the /append parameter. Copy the image to C:\remoteinstall\images.
Answer: A
Explanation:
Windows Deployment ServicesWDS provides a PXE-booted version of Windows PE. A WDS image is contained in a WIM file and is booted over the network into a RAMDisk. The installation then proceeds under Windows PE. The process of capturing a WIM image into a WDS server is similar to the use of ImageX and Sysprep except that the last step involves booting into the WDS capture image. This is a Windows PE image that helps you capture a client system to the WDS server. WDS is relatively lightweight compared to other image deployment methods such as MDT and provides a method that can be faster than an optical media-based installation of Windows. You use WDS images to deploy system files to client computers. A number of image files exist; for example, you use a capture image to create an install image. Install ImageAn install image is an operating system image that you deploy to the client computer. Typically, this is a WIM file.Boot ImageA boot image is a Windows PE image into which you boot a client before you install the WIM image file. To install Windows 7, you first boot the computer into the boot image, and then you select the install image to install. Unless you are using a reference computer and adding applications to the image, you should use the standard boot image that is included on the Windows 7 installation media (Install.wim). Capture and discover images are types of boot images. (need install image not boot)NOT OscdimgOscdimg is a command-line tool for creating an image file (.iso) of a customized 32-bit or 64-bit version of Windows PE. You can then burn that .iso file to a CD-ROM or DVD-ROM. Oscdimg supports ISO 9660, Joliet, and Universal Disk Format (UDF) file systems. (-boot : need install image not boot)NOT ImagexImageX is a command-line tool that enables original equipment manufacturers (OEMs) and corporations to capture, to modify, and to apply file-based disk images for rapid deployment. ImageX works with Windows image (.wim) files for copying to a network, or it can work with other technologies that use .wim images, such as Windows Setup, Windows Deployment Services (Windows DS), and the System Management Server (SMS) Operating System Feature Deployment Pack./appendAppends a volume image to an existing Windows image (.wim) file. Creates a single instance of the file, comparing it against the resources that already exist in the .wim file, so you do not capture the same file twice.
QUESTION 340
You have a computer that runs Windows 7. The computer has a single volume. You install 15 applications and customize the environment. You complete the following actions:
* Create an export by using Windows Easy Transfer. Create a system image by using Backup and Restore.
* Install the User State Migration Tool (USMT) and run Scanstate The disk on the computer fails.
You replace the disk. You need to restore the environment to the previous state. What should you do?
A. Install Windows 7, install USMT, and then run Loadstate.
B. Install Windows 7 and then import the Windows Easy Transfer package.
C. Start the computer from a Windows Recovery Environment (Windows RE) disk and then run Bcdboot. exe.
D. Start the computer from a Windows Recovery Environment (Windows RE) disk and then restore the system image.
Answer: D
Explanation:
Restoring from a System Image Backup. A System Image restore rewrites the entire contents of a system volume. Therefore, you restore from a System Image backup by booting from the Windows 7 Installation DVD- ROM and loading System Recovery tools or by pressing F8 during the boot process. Restoring from a System Image backup enables you to quickly get a computer running after you replace a failed hard disk, or if the operating system installation has been corrupted (for example, by malware that cannot be removed except 0 by wiping the disk). It is sometimes known as complete recovery or complete PC Restore. This procedure assumes that the System Recovery Options (otherwise known as the Windows Recovery Environment, or Windows RE) files are present on the DVD-ROM. If not, you can boot from the installation DVD-ROM and press F8 during the boot to access the Advanced Boot Options, as described in the next section of this lesson. To restore a System Image backup, perform the following steps:
1. Ensure the backup medium is connected to your computer.
2. Insert the Windows 7 DVD- ROM. Ensure that the computer BIOS is configured to boot from the DVD-ROM.
3. Restart your computer. When prompted to boot from DVD-ROM, press any key.
4. Windows 7 Setup loads. When prompted, select your regional preferences and then click Next.
5. Click Repair Your Computer.
6. In the System Recovery Options dialog box, click Restore Your Computer Using System Image. If thebackup was saved to a DVD-ROM, insert the DVD- ROM now. Click Next. The Windows System Image Restore Wizard starts.
7. On the Select A System Image Backup page, the most recent backup is automatically selected. If this is the backup you want to restore, click Next. Otherwise, click Select A System Image, click Next, and then select the desired backup.
8. On the Choose Additional Restore Options page, select the Format And Repartition Disks check box if you want to reformat the disk and overwrite all data, or if the disk is not formatted. If you do not want to overwrite all the data on your current disk, do not select this check box. Click Next.
9. Click Finish. When prompted, click Yes to confirm. Windows System Image Restore reads the data from the backup and overwrites existing files.
You can restore to a different-sized hard disk, provided that the hard disk is large enough to store the backup. After the restore is complete, the computer restarts using the restored system volume.
